Authentication
The OpenHIM offers a few authentication mechanisms to verify client interactions with the OpenHIM Core. These mechanisms are JWT Tokens, Custom Tokens, Mutual TLS and Basic Auth.
These Authentication mechanisms can be configured via JSON config files (see overview for more) or environment variables. The configured auth mechanisms will be displayed in the Client details section of the OpenHIM Console - screenshot below.
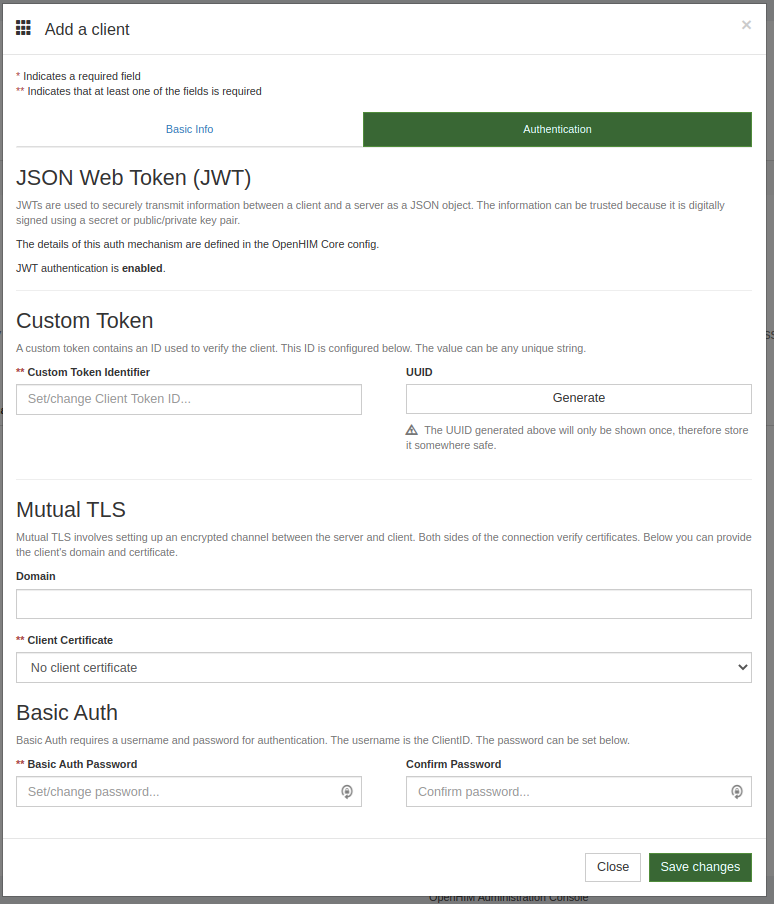
JSON Web Token(JWT)#
Useful Links:
See below for an example of a JWT token auth config.
JWT Auth is disabled by default
Tokens can be created in the JWT Sandbox for testing. The details from the JSON above are used in the screenshot below:
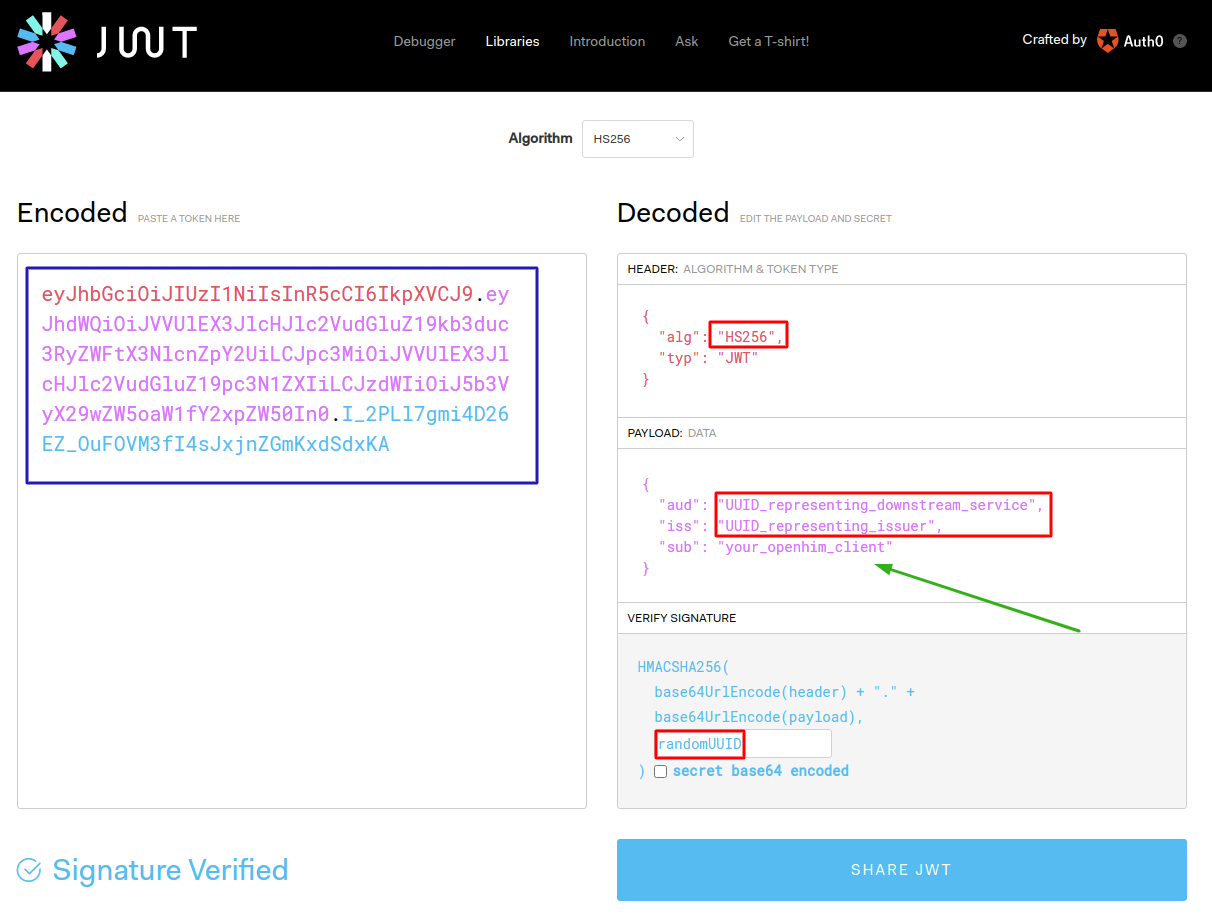
Remember to include your
client_idin thesub(subject) field of the JWT payload
The encoded token generated would then be used in the Authorization request header for requests to the OpenHIM Core:
Custom Token#
The Custom Token is a string value associated with a specific client. This value is sent in the request header to verify the client's identity. To enable Custom Tokens, the following config line is required:
Custom Token Auth is disabled by default
A user will have to add the token in the Clients section on the OpenHIM Console. This token will then be added to the authorizaton header of a request as follows:
Mutual TLS#
To enable Mutual TLS, the following config line is required:
Mutual TLS Auth is enabled by default
To make use of this Auth mechanism for a Client, you will first need to add your certificate to the OpenHIM in the Certificates section. You could also generate your own trusted client certs from the OpenHIM Console. See the certificates section for details. You may then choose one of the available client certificates from the Client Certificate drop down. To send through a test request via Postman, see this guide.
When sending secure requests to the OpenHIM Core remember that the default HTTPS port is
5000
Basic Auth#
For this authentication mechanism, the username and password are used. The OpenHIM Core JSON config must contain the following line in the authentication section.
Basic Auth is enabled by default
From the OpenHIM Console, Clients can be added and their Basic Auth details managed from the Clients section.
The request should look something like this: